Native Intelligence Provides CMMC-compliant Security Awareness Training
By: K Rudolph • March 25, 2020

K Rudolph
A published author and an experienced editor and document designer, K's mission is to help authors do great work.
Estimated read time:
What is the CMMC?
The Cybersecurity Maturity Model Certification (CMMC) is a new initiative by the Department of Defense, scheduled to be enforced in late 2020. Once the CMMC is established, DoD prime and subcontractors will be restricted from new contracts unless their computer security program meets CMMC requirements. And, unlike past acquisition requirements, with the CMMC, contractors will not be allowed to self-certify their compliance. They will need to be audited by a third-party cybersecurity firm.
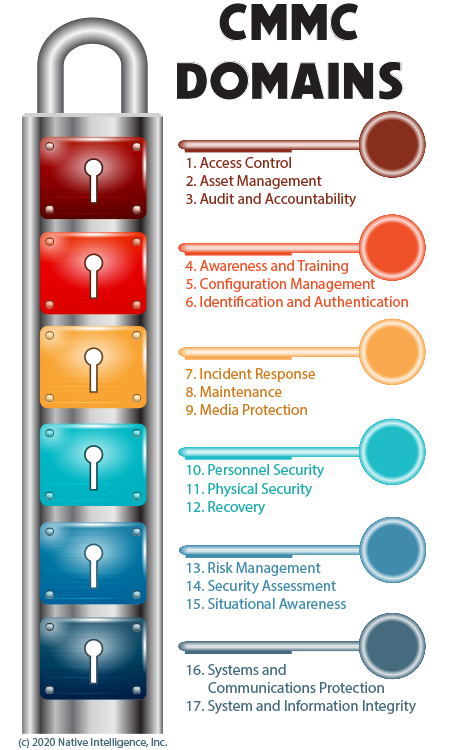
The CMMC includes five maturity levels, (Levels 1–5) that establish cybersecurity requirements based on the sensitivity of the contractor's work. Level 1 applies to all contractors, with each level increasing requirements until Level 5, which is only for the most sensitive programs (such as weapons development).
CMMC Capability C011 Conduct Security Awareness Activities
The CMMC domain “Awareness and Training (AT)” is concerned with ensuring that organizations have a formal security training program. Performing formal training is required at CMMC maturity levels 2 and above.
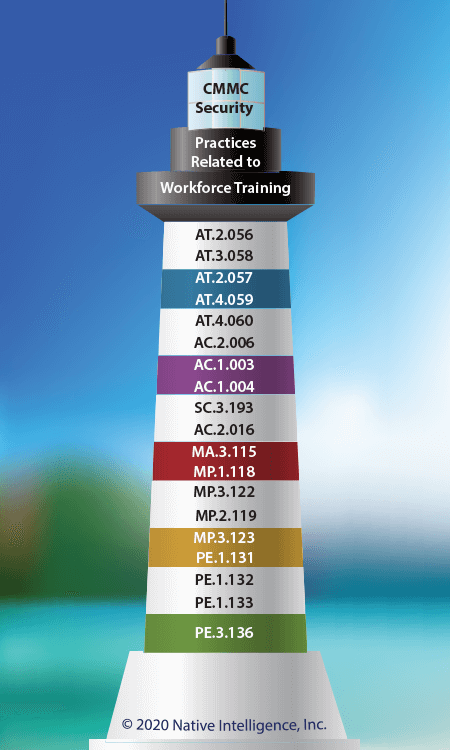
AT.2.056 – "Cybersecurity awareness training for all users."
“Ensure that managers, system administrators, and users of organizational systems are made aware of the security risks associated with their activities and of the applicable policies, standards, and procedures related to the security of those systems.”
This level 2 requirement is covered by annual cybersecurity awareness training. Your workforce needs to understand that their actions could weaken security or allow bad actors onto the network. The training program should be customizable to include links to your organization’s policies and to display contact information for your security department.
AT.3.058 — “Provide security awareness training on recognizing and reporting potential indicators of insider threat.”
Contractors that deal with Controlled Unclassified Information (CUI) need to add insider threat training. This training should describe the risk factors for becoming an insider threat (such as mental illness, dissatisfaction, and intent towards espionage). It should also give methods for reporting potential insider threats that are less formal… since these individuals are often friends as well as co-workers.
CMMC Capability C012 Conduct Training
AT.2.057 — “Ensure that personnel are trained to carry out their assigned information security-related duties and responsibilities.”
Contractors should have security training specific to developers, helpdesk, testing, and system administrator personnel. This can be handled with a system administrator-specific training course or via security certifications like the SECURITY+ certification.
Your security personnel (such as your CISO) should have advanced training and certifications, such as the CISSP.
AT.4.059 — “Provide awareness training focused on recognizing and responding to threats from social engineering, advanced persistent threat actors, breaches, and suspicious behaviors; update the training at least annually or when there are significant changes to the threat.”
AT.4.060 — “Include practical exercises in awareness training that are aligned with current threat scenarios and provide feedback to individuals involved in the training.”
These two best practices are for level 4+ organizations, those that are targeted by advanced threat actors. Annual awareness training from Native Intelligence meets the requirements in AT.4.059.
To meet AT.4.060, you will need to add practical exercises to the curriculum. This can be accomplished with a specialized course that gives realistic examples of threats and asks users to respond to them (such as our phishing course). Another option is to test your users with simulated phishing attacks; these come to their real email.
Security Awareness Training for 14 Other CMMC Practices
Cybersecurity awareness and training are a great way to handle 14 more practices in the CMMC. These practices are in the domains:
- • Access Control (AC),
- • Media Protection (MP),
- • Physical Protection (PE), and
- • Systems and Communications Protection (SC).
The 14 practices below require broad agreement and compliance from your workforce. Even with the best technical controls, if your workers take the wrong action, they could cause your security to fail. This is why we recommend including these topics in your security awareness training.
AC.2.006 — “Limit use of portable storage devices on external systems.”
Your workforce should be trained not to connect corporate thumb drives and external hard drives to home computers or other untrusted systems.
AC.1.003 — “Verify and control/limit connections to and use of external information systems.”
Users should be trained to use only corporate or government systems for work, especially sensitive work.
AC.1.004 — “Control information posted or processed on publicly accessible information systems.”
Users should be warned against saving work files to public clouds such as OneDrive and Google Drive, which are common sources of DoD data breaches.
SC.3.193 — “Implement a policy restricting the publication of CUI on externally owned, publicly accessible websites (e.g., forums, LinkedIn, Facebook, Twitter).”
Training needs to address other means of accidentally disclosing sensitive information (such as ship movements). This is normally done by advising users to not discuss work on their social media accounts.
AC.2.016 — “Control the flow of CUI in accordance with approved authorizations.”
Users need to know what Controlled Unclassified Information (CUI) is and how to recognize it, along with other categories of sensitive information. Training should give clear guidance about how to send sensitive information securely (such as with encrypted emails) and verification of recipients.
MA.3.115 — “Ensure equipment removed for off-site maintenance is sanitized of any CUI.”
MP.1.118 — “Sanitize or destroy information system media containing Federal Contract information before disposal or release for reuse.”
All employees need to understand that computer equipment must be returned to the IT department rather than throwing it in the trash or selling it. The same training topic will also teach users to shred sensitive documents and CDs / DVDs.
MP.3.122 — “Mark media with necessary CUI markings and distribution limitations.”
All employees need to understand how to mark sensitive files and data. Your training should include custom sections for the specific types of CUI your users will encounter.
MP.2.119 — “Protect (i.e., physically control and securely store) system media containing CUI, both paper and digital.”
All users need to know the standards for protecting sensitive data, such as locking it up when unattended. This is particularly important for teleworkers and those who work out of alternate locations.
MP.3.123 — “Prohibit the use of portable storage devices when such devices have no identifiable owner.”
Users are the prime target for advanced threat actors. They need to know that portable storage devices can be infected with malware and not to connect them to the corporate network.
PE.1.131 — “Limit physical access to organizational information systems, equipment, and the respective operating environments to authorized individuals.”
PE.1.132 — “Escort visitors and monitor visitor activity.”
PE.1.133 — “Maintain audit logs of physical access.”
User training is the best way to get everyone on the same page about protecting your facility. Topics should include identifying and reporting unauthorized persons, procedures for escorting visitors, and how to prevent tailgating.
PE.3.136 — “Enforce safeguarding measures for CUI at alternate work sites.”
This topic is essential for teleworkers and those who work at customer sites. Training should address best practices for protecting CUI outside of the office, such as not printing it out, and making sure the computer is locked whenever the user steps away.
Integrating Training and Policies for CMMC Compliance
Bottom line: Regular awareness training is more effective than policies and procedures alone. The course certificate and LMS records document that your users reviewed the material and quiz. Training your workforce helps prevent financial and reputational loss.
It's time to review your cybersecurity awareness training to be sure that it addresses each of the above CMMC practices.
Native Intelligence Security Awareness Courses Help You Comply with the CMMC
Native Intelligence training courses are engaging. They include interesting stories, practical exercises, real examples of cyber threats, exercises, and a final quiz with a score and certificate. Our CMMC-compliant awareness course is designed to be easily customized with your information.
We offer all hands training on general topics and phishing, privileged-user training for secure development and administration, monthly newsletters, and weekly email tips to break security into digestible chunks.
We are happy to customize our courses to fit your organization’s security policies, reporting methods, and branding.
Request a Demo of Our CMMC-compliant Training
Please request a free demo of our CMMC-compliant security awareness course by filling out the contact form, calling us at (410) 531-1396, or emailing us at info@nativeintelligence.com.